The Rasith.A worm propagates through removable devices. When an infected device is connected to a computer, the malware’s hidden files execute without the user’s knowledge or consent. The worm is self-replicating and steals sensitive system information, thereby continuing its spread. As a standalone malware program, a computer worm seeks to spread to other computers by self-replication.
- ( Please note that the “Windows Error” window image provided earlier is no longer functional and no longer appears due to compatibility issues with Windows 10 and 11. However, the worm’s ability to spread through removable media drives still persists in Windows 10, but not in Windows 11. It is worth noting that many users may not even notice any changes in their removable media drive folders once it is infected. )
Regrettably, the Rasith.A worm has become a common and popular malware variant, with a significant impact on the government office computers in Sri Lanka. The worm shares similarities with the shortcut virus, which has also been widespread in Sri Lanka.
The Rasith.A worm exclusively targets Windows-based computers.
A hidden file named kabe.exe is responsible for infecting a computer from within a pen drive. In some cases, all the folders on the device may be hidden, with malicious executables posing as normal Windows folders with a changed custom file icon. When the user attempts to open one of these folders, the file executes, and the folder appears to open as usual. This behavior is reminiscent of the shortcut virus.
- With “Hide extensions for known filetypes” enabled
- With “Hide extensions for known filetypes” disabled

NOTE: To see all the hidden files, run this command
attrib -h -r -s /s /d *.*
Upon executing, the Rasith.A worm generates an executable file called msfold.exe at C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\msfold.exe. Once this file runs for the first time, it creates a copy of itself at C:\Users\admin\AppData\Local\Temp\explorer.exe, giving itself the same name as a legitimate system process (explorer.exe) and blending in with other processes in the Task Manager.
The worm also creates two superfluous temporary files at C:\Users\admin\AppData\Local\Temp. Although these files appear to be useless, they are nonetheless generated every time the worm executes.
The Rasith.A worm creates or modifies an AUTORUN.INF file in the removable media drive. This file is hidden, and its contents are as follows:
[AutoRun]
action=Open
shell\execute=kabe.bat
shell\explore\command=kabe.bat
USEAUTOPLAY=1
shell\Open\command=kabe.bat
shell\Autorun\command=kabe.bat
shell\Search\command=kabe.bat
These settings indicate that the worm aims to run the kabe.bat file. When executed, the kabe.bat file launches kabe.exe, which subsequently triggers the worm’s full activation.
The new explorer.exe file generated by the Rasith.A worm temporarily creates a SQLite3 database file at C:\Users\admin\AppData\Local\Temp\sajith_and_rasini.db. Another database file with the name i_love_you_rasini.db can also be observed. It is unclear why these two files are generated, but they may be intended to mislead the user. However, given the nature of the worm, the purpose behind these files is uncertain.
To summarize the actions of the Rasith.A worm, the malware performs the following tasks:
-
Drops the executable file immediately after the start
-
Writes to the Start menu file
-
Drops a file with too old compile date
-
Starts itself from another location
-
Executable content was dropped or overwritten
-
The process creates files with names similar to system file names
-
Creates executable files that already exist in Windows
-
Creates files or folders in the user directory
-
Reads the computer name
-
Reads the machine GUID from the registry
-
The process checks LSA protection
-
Create files in a temporary directory
-
Checks supported languages
-
Registry Access
Path: "\REGISTRY\MACHINE\SYSTEM\CONTROLSET001\CONTROL\COMPUTERNAME\ACTIVECOMPUTERNAME", Key: "COMPUTERNAME"
Path: "\REGISTRY\MACHINE\SOFTWARE\MICROSOFT\CRYPTOGRAPHY", Key: "MACHINEGUID"
- Reads Configuration Files
read file "C:\Users\desktop.ini"
read file "C:\Users\%USERNAME%\desktop.ini"
read file "C:\Users\%USERNAME%\Desktop\desktop.ini"
read file "%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\desktop.ini"
read file "C:\Users\%USERNAME%\Desktop\desktop.ini"
- Creates files in windows directory
created file "C:\Windows\Globalization\Sorting\sortdefault.nls"
created file "C:\Windows\system32\rsaenh.dll"
created file "C:\Windows\Fonts\staticcache.dat"
created file "C:\Windows\system32\wshom.ocx"
created file "C:\Users\%USERNAME%\AppData\Local\Microsoft\Windows\Caches"
created file "C:\Users\%USERNAME%\AppData\Local\Microsoft\Windows\Caches\cversions.1.db"
created file "C:\Users\%USERNAME%\AppData\Local\Microsoft\Windows\Caches\{AFBF9F1A-8EE8–4C77-AF34-C647E37CA0D9}.1.ver0x0000000000000006.db"
created file "%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu"
created file "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\desktop.ini"
- Drops executable files
"explorer.exe" has type "PE32 executable (GUI) Intel 80386, for MS Windows"
"msfold.exe" has type "PE32 executable (GUI) Intel 80386, for MS Windows"
- Potential URL found in binary/memory
Email - allosfix@hotmail.com
Here’s a professional version of the text you provided:
The Rasith.A worm is associated with the email address allosfix@hotmail.com. The malware was originally developed using VB 6, an older programming language, and was detected by antivirus software at the time of its initial release. However, it appears to have evaded detection in recent years for unknown reasons.
To remove the Rasith.A worm from your computer, follow these steps:
-
Restart your computer in safe mode
-
Locate the following files and delete them:
C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\msfold.exeC:\Users\admin\AppData\Local\Temp\sajith_and_rasini.dbC:\Users\admin\AppData\Local\Temp\i_love_you_rasini.db
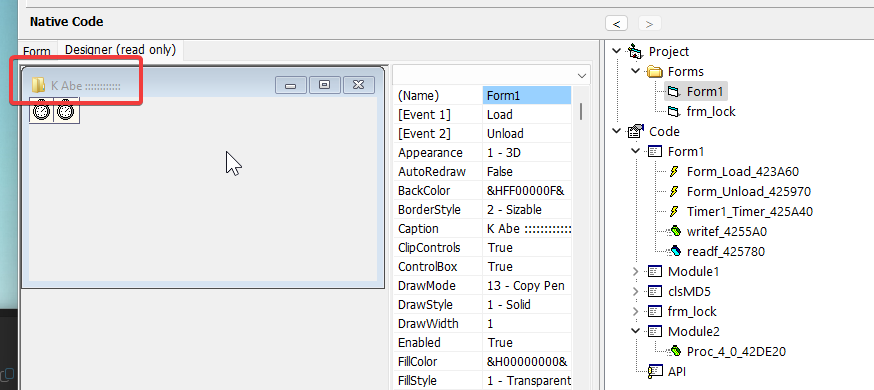
Upon decompiling the Rasith.A worm with VB Decompiler Lite v12, it was discovered that the file is actually named “K Abe”, rather than “kabe” as initially believed. The naming convention, coupled with the creation of the .db files with names such as sajith_and_rasini.db and i_love_you_rasini.db, suggests a Sri Lankan origin for the malware creator. However, it is important to note that definitive conclusions about the creator’s nationality cannot be drawn with certainty when analyzing malware.
- its called
K Abeand notkabe
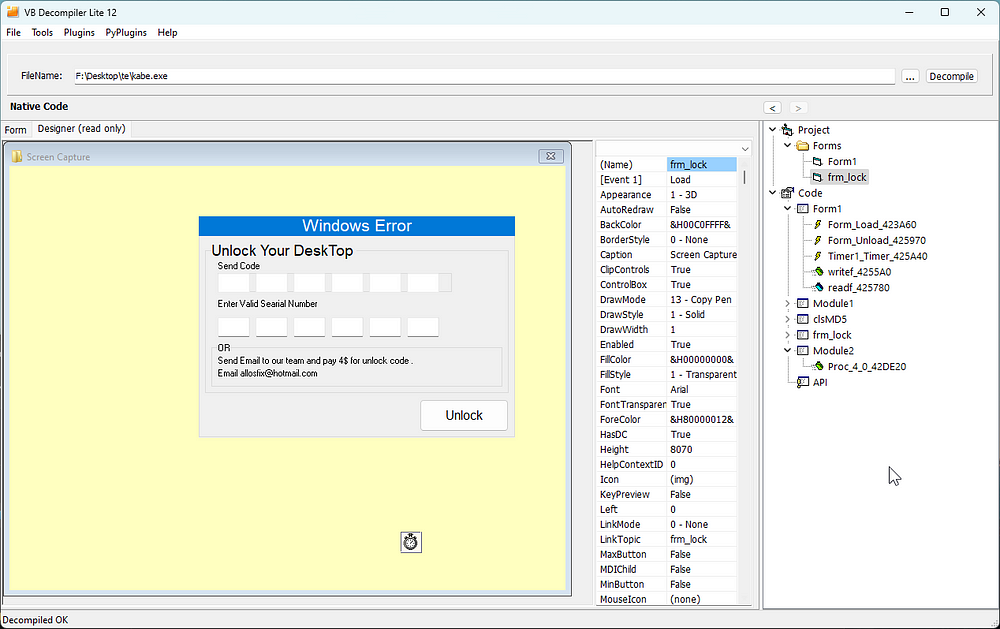
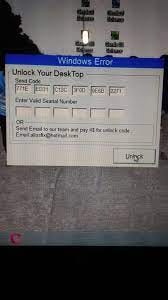
- The form that you get promptet with, made with Visual Basics 6 (this is what you got prompted with, this doesnt work anymore)
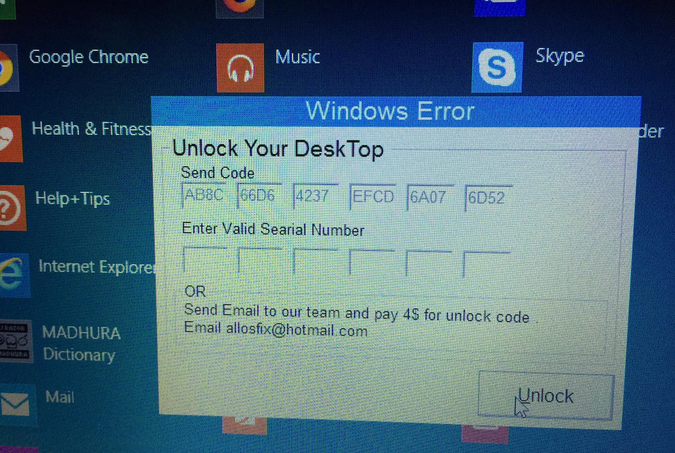
It is notable that the attacker is only asking for a ransom of $4, which is a relatively small amount. This could be an indication that the attacker is not particularly skilled or motivated, or that they are specifically targeting low-value targets, or maybe he’s from a country where 4$ is a huge amount. Alternatively, it could be a deliberate attempt to avoid attracting too much attention or to make the ransom demand more likely to be paid. Nonetheless, regardless of the amount requested, it is important to never pay a ransom to attackers, as it encourages their criminal activities and does not guarantee that access to the infected system will be restored.
The decompiled file project information reveals the following details:
Type=Exe
Reference=*\G{00020430-0000-0000-C000-000000000046}#2.0#0#..\..\..\..\WINDOWS\SYSTEM32\STDOLE2.TLB#OLE Automation
Form=Form1.frm
Module=Module1; Module1.bas
Class=clsMD5; clsMD5.cls
Form=frm_lock.frm
Module=Module2; Module2.bas
Startup="Form1"
IconForm="Form1"
HelpFile=""
ExeName32="sajith.exe"
Name="Project1"
Title="sajith"
VersionCompanyName="Folders"
MajorVer=1
MinorVer=00
RevisionVer=0
Command32 = ""
HelpContextID = "0"
CompatibleMode = "0"
AutoIncrementVer = 0
ServerSupportFiles = 0
CompilationType = 0
OptimizationType = 0
FavorPentiumPro(tm) = 0
CodeViewDebugInfo = 0
NoAliasing = 0
BoundsCheck = 0
OverflowCheck = -1
FlPointCheck = 0
FDIVCheck = 0
UnroundedFP = 0
StartMode = 0
Unattended = 0
Retained = 0
ThreadPerObject = 0
MaxNumberOfThreads = 1
[MS Transaction Server]
AutoRefresh = 1
[VB Decompiler]
Build = 12.0.8439.29532
Date = 2/15/2023
- Additional images of infected computers:
Upon investigation, it is evident that the malware attempts to access the IPv4 address of 20.99.184.37, which is owned by Microsoft. This suggests that the attacker utilized a Microsoft Azure server as a command and control center to manage the worm and collect the $4 ransom. Further details regarding the IP address can be found at here. It is worth noting that Microsoft has already taken this down.
As this is an older program, its functionality may not work as intended by the attacker on modern computers and newer operating systems. However, despite any limitations, the program is designed to continue running and spreading.
Sources: